- Sharing your code with others through a public Replit App or copy-paste
- Checking your code into version control in a public repository
- Live streaming or screen sharing your code
Features
Secrets include the following features:- End-to-end encryption: Automatically protect your data using AES-256 encryption at rest and TLS encryption in transit
- App-level secrets: Store and manage secrets that are specific to a Replit App
- Account-level secrets: Store and manage secrets that you can make available across all your Replit Apps
- Environment variable access: Access your secrets from your code using environment variables
- Collaborative access: Share secrets with collaborators and team members
Usage
Secrets are available for all deployment types except Static Deployments.
How to access Secrets
How to access Secrets
From the left Tool dock:
- Select
All tools to see a list of workspace tools.
- Select
Secrets.
- Select the
magnifying glass at the top to open the search tool
- Type “Secrets” to locate the tool and select it from the results.
Manage App Secrets
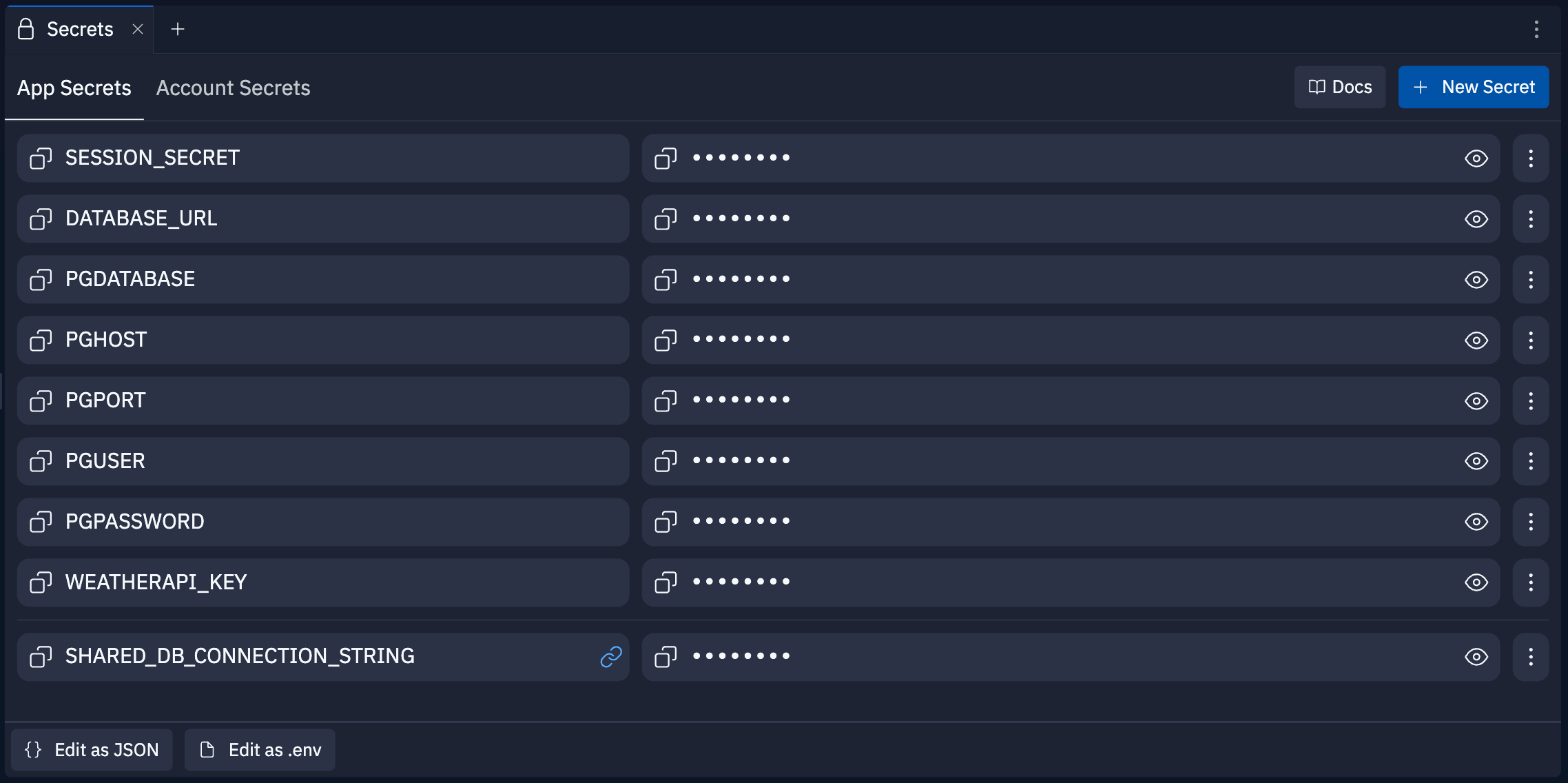
You can manage your app-level secrets in the App Secrets tab in the Secrets pane. This tab displays a list of all secrets associated with your Replit App.Add App Secrets
Add App Secrets
To add a secret:
- Select New Secret.
- Enter a Key, the name of the secret, and a Value, the secret itself.
- Select Add Secret to save the entry.
Edit App Secrets
Edit App Secrets
To edit a secret:
- Select the
vertical dots menu next to the secret.
- Select Edit from the contextual menu.
- Update the text in the Key or Value field and select Update Secret to save changes or Cancel to discard changes.
View App Secrets
View App Secrets
To view a secret, select the  eye icon next to the secret.To hide the secret, select the
eye icon next to the secret.To hide the secret, select the  eye with slash icon.
eye with slash icon.
Delete App Secrets
Delete App Secrets
To delete a secret, select the  vertical dots menu next to the secret and select Delete.
vertical dots menu next to the secret and select Delete.
Manage Account Secrets
You can manage your account-level secrets in the Account Secrets tab in the Secrets pane. This tab displays a list of only secrets associated with your Replit account.Add Account Secrets
Add Account Secrets
To add an account-level secret:
- Navigate to the Account Secrets tab.
- Select
Manage Account.
- Select New Secret to add a secret.
- Enter a Key, the name of the secret, and a Value, the secret itself.
- Select Save to save the entry.
Edit Account Secrets
Edit Account Secrets
To edit a secret:
- Select the
pencil icon next to the secret.
- Update the text in the Key or Value field and select Save to save changes or Cancel to discard changes.
View Account Secrets
View Account Secrets
To view a secret, select the  eye icon next to the secret.To hide the secret, select the
eye icon next to the secret.To hide the secret, select the  eye with slash icon.
eye with slash icon.
Link Account Secrets
Link Account Secrets
To use an account-level secret in a Replit App, you must link it to the app.
To link an account-level secret:
- Navigate to the App Secrets tab.
- Select the checkbox to the left of the secret.
- Select Link to this App.
- Navigate to the App Secrets tab.
- Select the
vertical dots menu next to the secret.
- Select Unlink.
Delete Account Secrets
Delete Account Secrets
- Select the
pencil icon next to the secret.
- Select Delete.
Access secrets in your code
Managing secrets visibility
Secrets visibility depends on your access to a Replit App and whether you authored it. You can use one of the options to share your Replit App:- Multiplayer: Invite Replit users to collaborate in real-time
- Cover page: Show a preview of your Replit App with the option to remix it
- Remix: Make your individual or organization’s Replit App public so others can create their version
| Access Method | Who | Can See Names | Can See Values |
|---|---|---|---|
| Multiplayer | Multiplayer collaborator | ✓ | ✓ |
| Multiplayer | Organization member (Owner role) | ✓ | ✓ |
| Multiplayer | Organization member (Non-owner) | ✓ | |
| Cover Page | Any visitor | ||
| Remix | Owner/collaborator remixing own Replit App | ✓ | ✓ |
| Remix | Non-owner/collaborator remixing Replit App | ✓ | |
| Remix | Anyone remixing from cover page | ✓ | |
| Organization Remix | Organization member with Owner role | ✓ | ✓ |
| Organization Remix | Organization member without Owner role | ✓ |
Database and storage related secrets
When you add Replit’s database or object storage, the workspace automatically creates the following secrets:| Secret | Description |
|---|---|
DATABASE_URL | SQL database connection string |
PGHOST | PostgreSQL hostname |
PGUSER | PostgreSQL username |
PGPASSWORD | PostgreSQL password |
PGDATABASE | PostgreSQL database name |
PGPORT | PostgreSQL port |
printenv in the Shell workspace tool or print them from your code.
Predefined environment variables
Replit automatically sets the following environment variables that you can access from your app:| Environment Variable | Description |
|---|---|
REPLIT_DOMAINS | Comma-separated list of all domains associated with your Replit App |
REPLIT_USER | Username of the current editor, which may vary in Multiplayer sessions |
REPLIT_DEPLOYMENT | Set to 1 if the code is running in a published app, unset otherwise |
REPLIT_DEV_DOMAIN | Development URL on the replit.dev domain, which is different from the Deployment URL |
os.environ object or running printenv in the Shell.