Features
Replit Teams and Enterprise provides comprehensive access control through two complementary systems that work together to manage access across your organization.Admin
Full administrative access to organization settings and all resources
Member
Can see all other members and create Apps and Projects
Guest
Limited access to only shared apps and resources
Viewer
Read-only access to apps and deployments
- Default roles: Four built-in access levels that provide baseline access control for all team members
- Custom groups: Create specialized groups for fine-grained access control beyond default role limitations
- Flexible access control: Use roles and groups to grant precise access for different Apps and resources
- Easy member management: Add, remove, and transfer members between groups with simple administrative controls
Usage
Roles
Every team member must have a role that defines their baseline access level within your organization. Admins assign roles when adding new members to ensure proper access control from day one. The four default roles provide different levels of access:- Admins: Have access to every action available in Replit Teams, including organization settings, billing, and member management
- Members: Can create and edit Replit Apps and see all other team members, but cannot perform sensitive administrative actions
- Guests: Have the lowest access level and can only edit apps specifically shared with them. This role is useful for external contractors or interview candidates
- Viewers: Have read-only access to apps and deployments, making them ideal for stakeholders who need visibility without editing capabilities
Custom groups
Custom groups provide more access control beyond default roles. Create groups to grant specific access to selected team members while maintaining their base role access.For information on syncing IdP groups to Replit for easier bulk user access management, see SCIM.
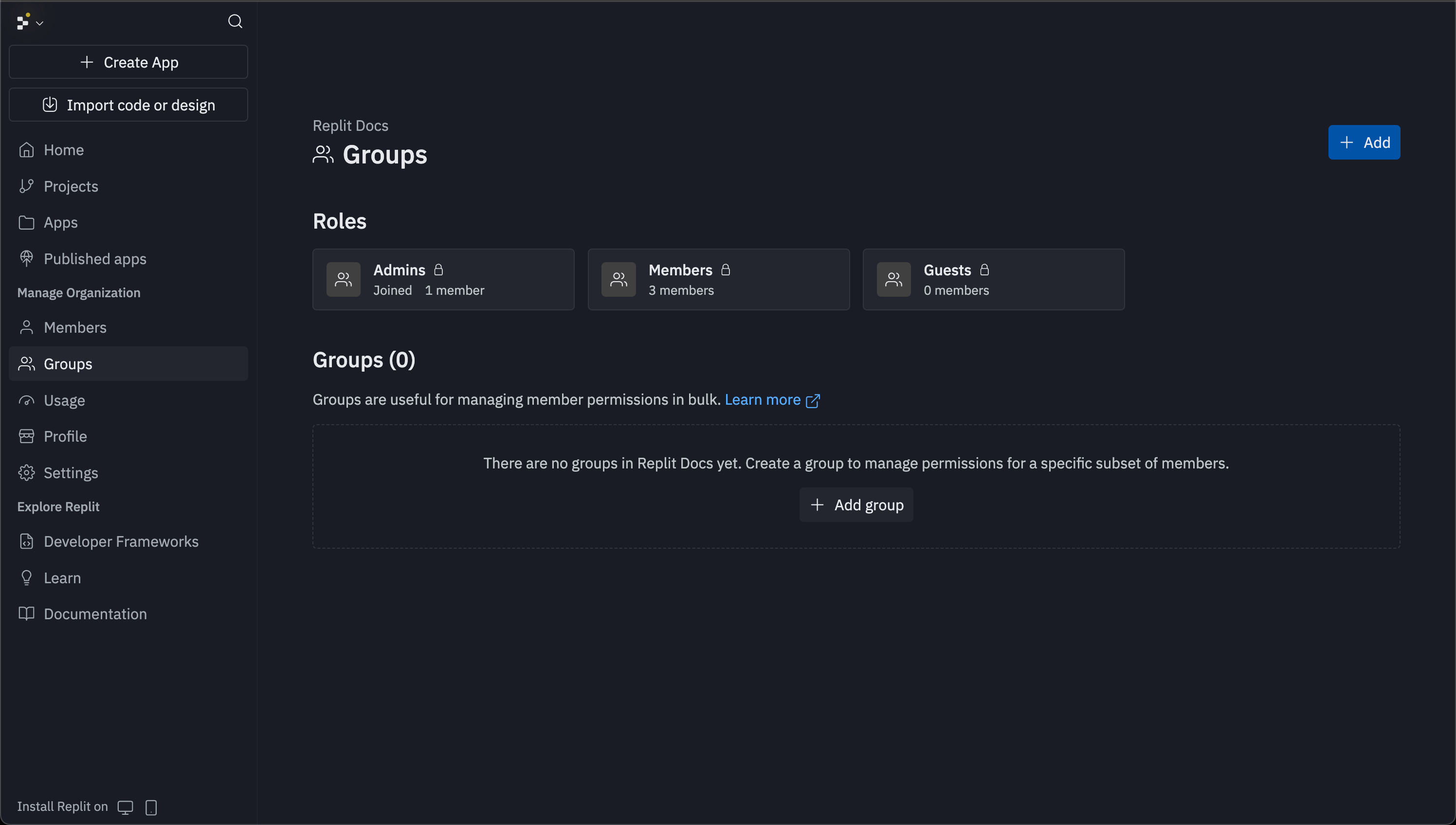
Creating a group
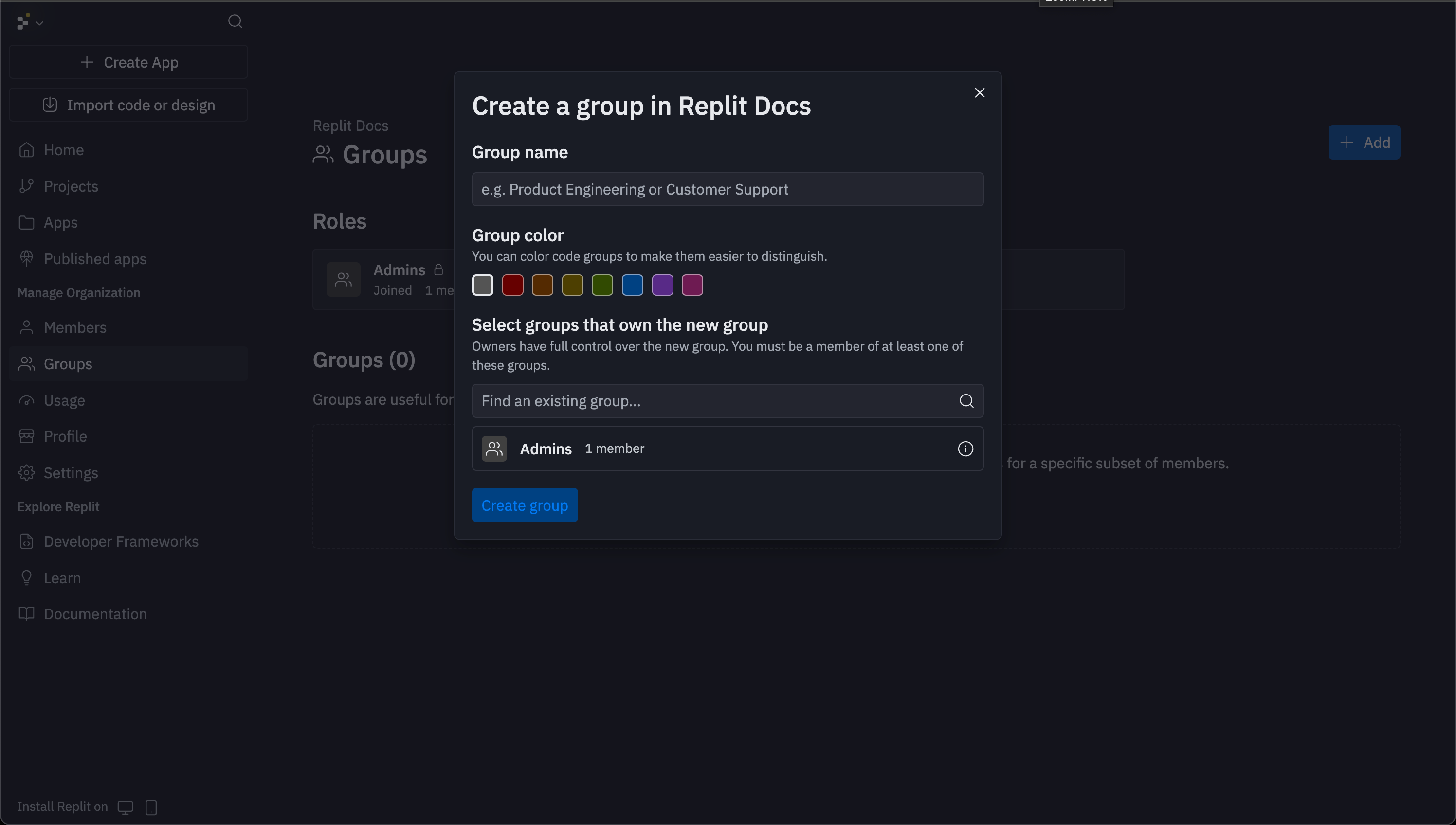
Admins can create unlimited custom groups from the groups page. Select the Add button in the top right corner to open the creation modal where you can:- Name your group: The group name is the only required field
- Add visual identifiers: Choose colors and icons to distinguish groups
- Assign members: Add team members to groups individually or in bulk
- Grant access: Groups can later receive access to specific apps through each app’s Invite button
Managing groups
Select any group card to access its management interface. Group management includes member addition, removal, and permissions configuration.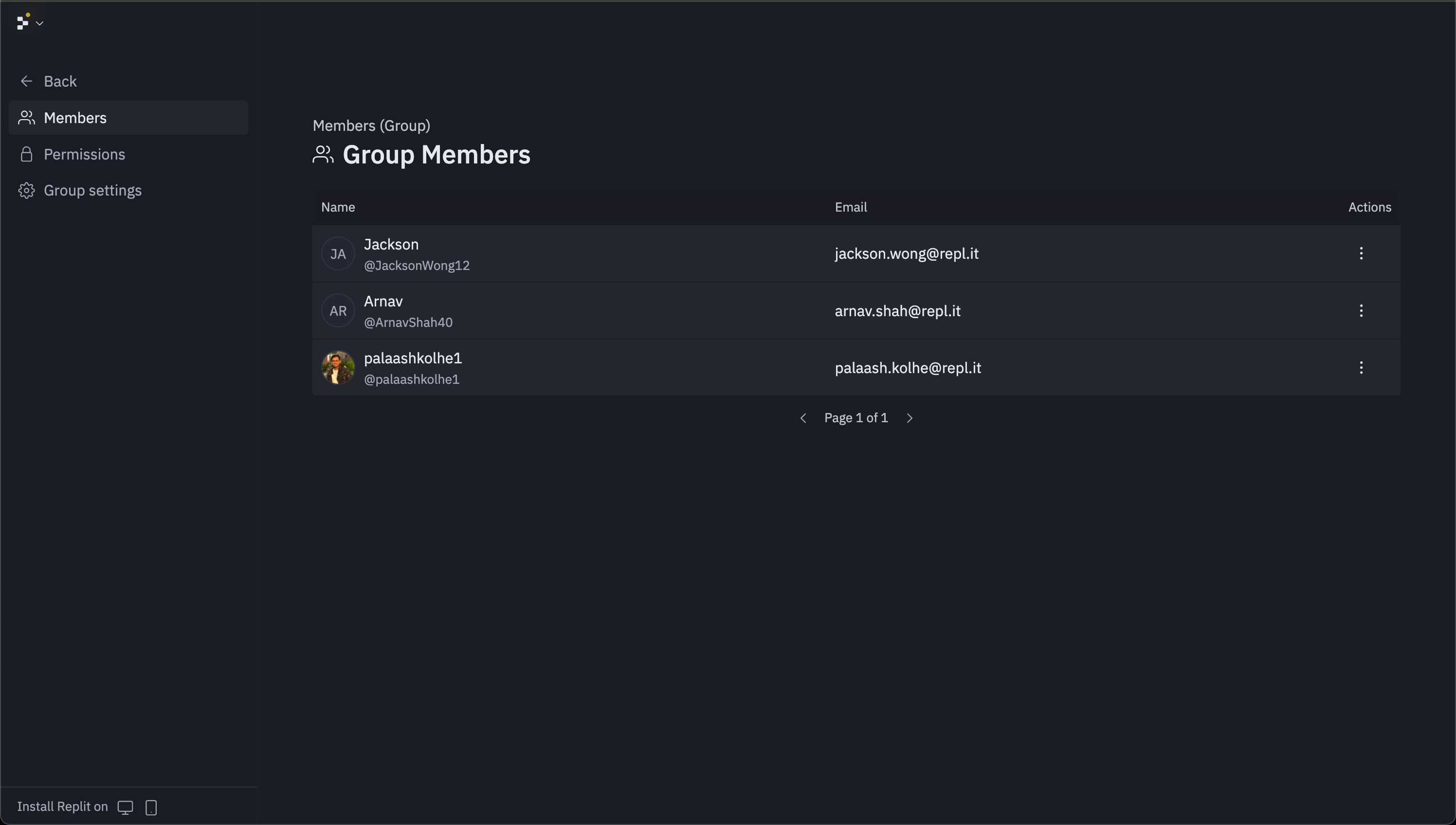
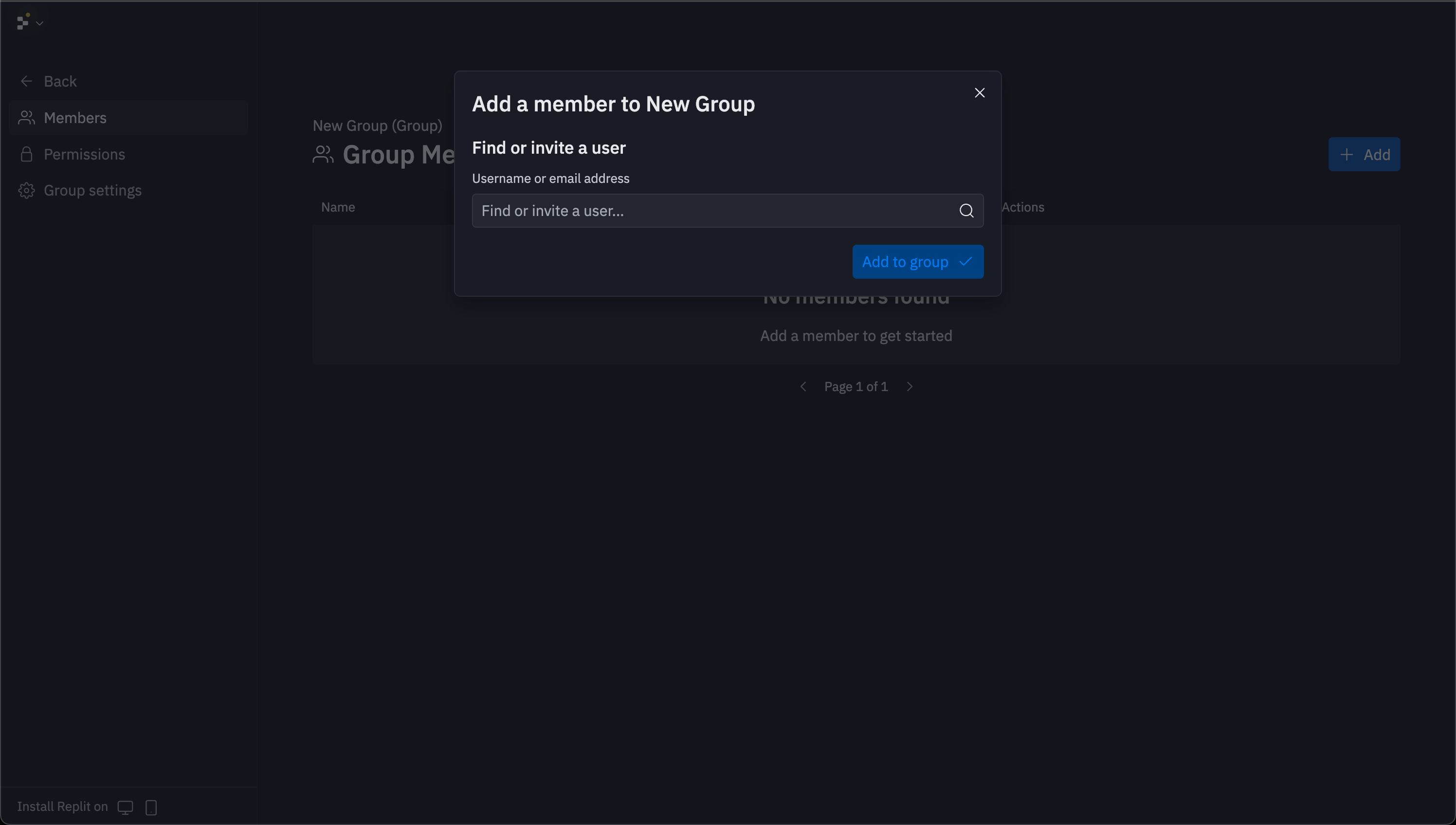
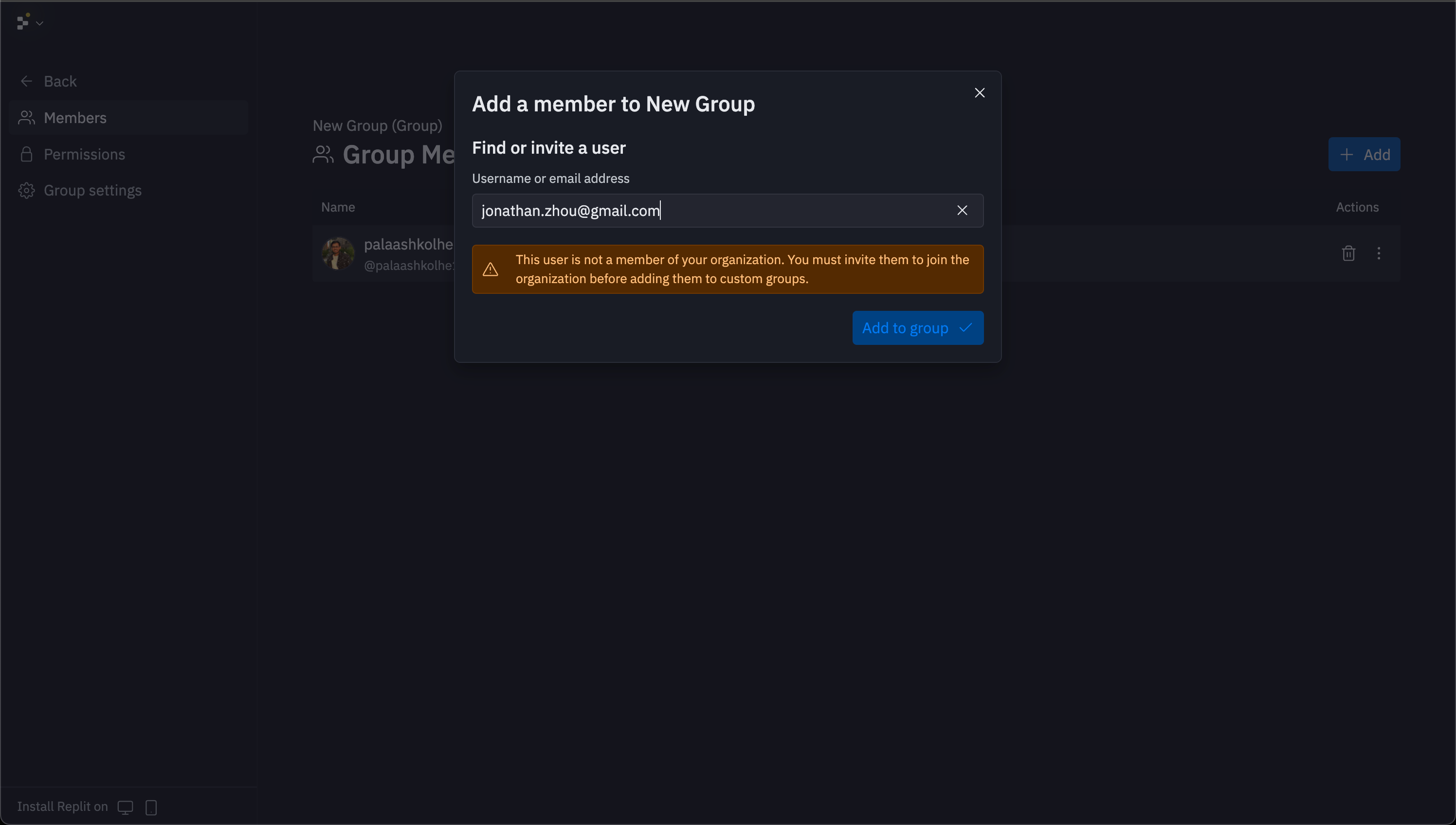
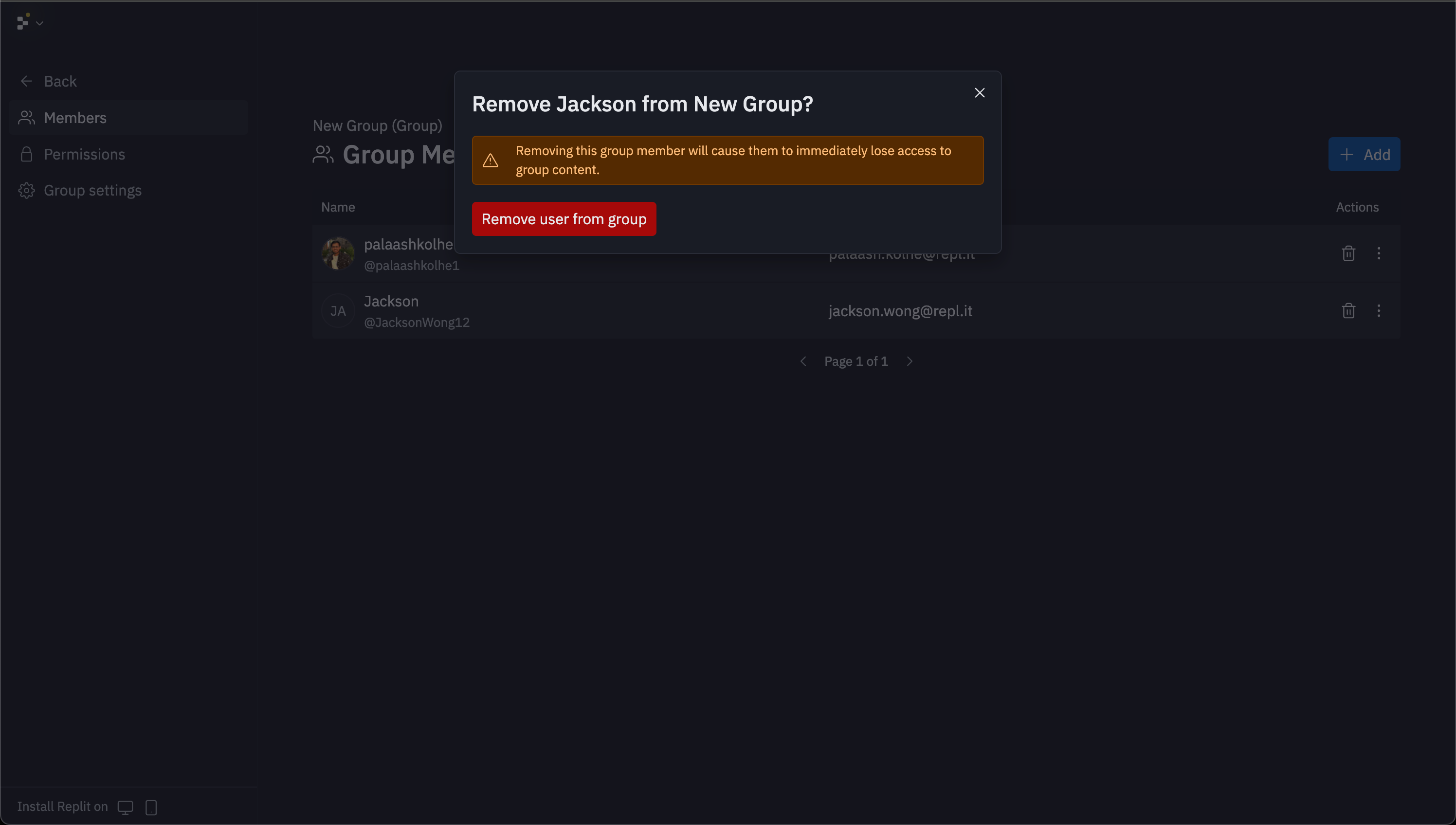
Setting group permissions
Assign organizational permissions to groups to define what level of access group members must have in your organization. To set group permissions, select the created group and choose the permissions tab in the left navigation. The available permissions levels are:- Owner: Can perform all organization actions, including deleting the organization
- Billing manager: Can update the organization’s payment information, add and remove seats, and set spending limits
- Manager: Can create and manage groups, add and remove organization members, and view billing information
- Editor: Can create new Apps and view usage information
- Viewer: Can see basic information about the organization
App access control
Control who can access and collaborate on your apps using Replit’s Access feature. Assign access to roles and groups to share specific apps with the right team members while maintaining security across your organization.Setting app access
How to manage app access
How to manage app access
From any app, select Invite in the upper right corner (to the left of Publish) to open the Access panel.
- Default roles: Admin, Members, Guests, and Viewers appear automatically in the Access panel
- Custom groups: Use the search functionality to find and grant app access to specific custom groups
Access levels
You can assign different access levels to each role and group for fine-grained control:- Owner: Full access including app deletion and administrative control
- Publisher: Can edit code, republish apps, and manage app resources, and settings
- Editor: Can edit code and view app resources without publishing capabilities
- Viewer: Read-only access to code with the ability to fork apps for their own use
- None: No access to search, view, or edit the app