Accessing privacy settings
How to access Privacy Settings
How to access Privacy Settings
- Navigate to your enterprise workspace
- Select Settings
- Select Advanced to view all available settings
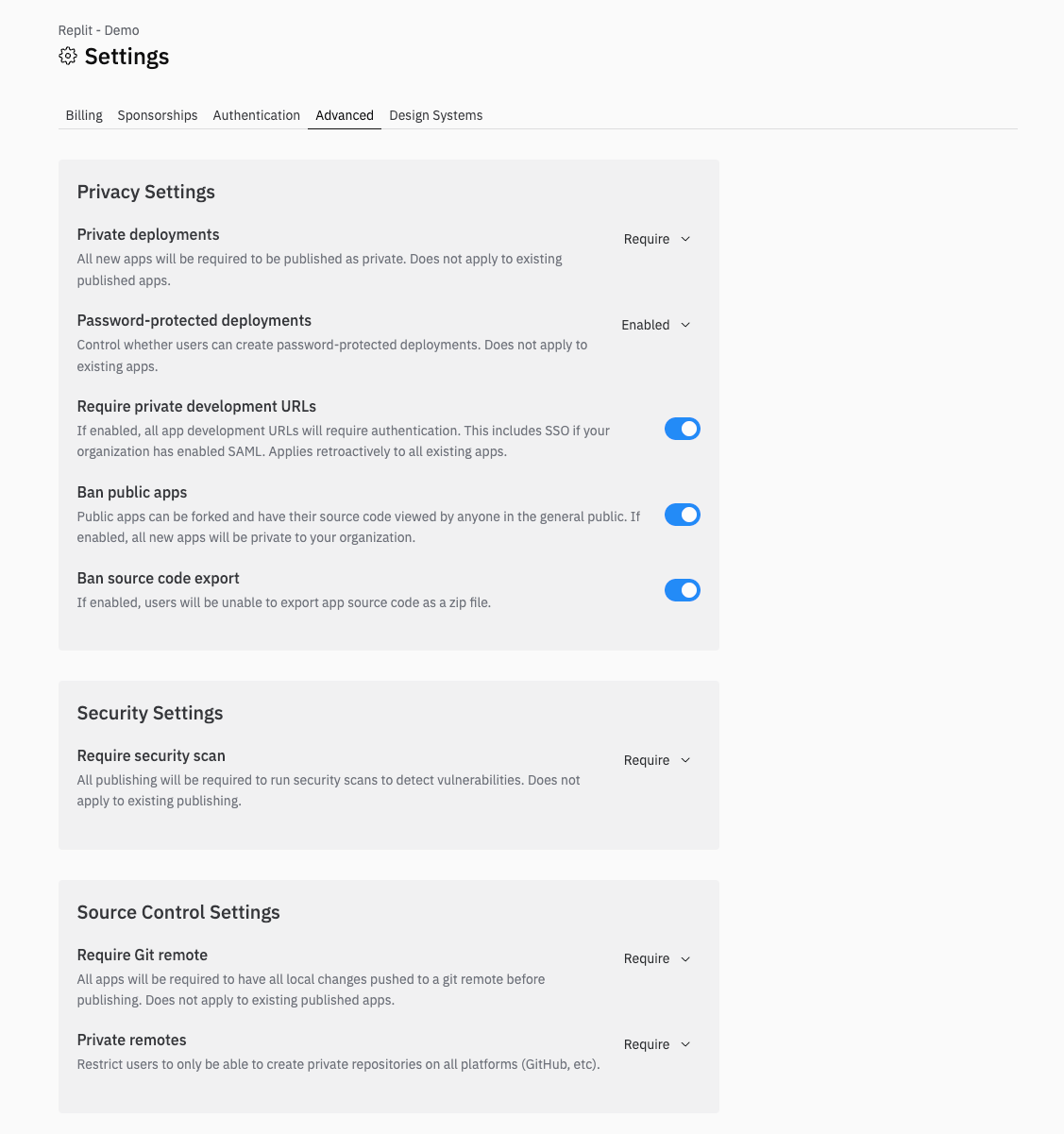
Privacy settings
Privacy settings control how apps are published and accessed within your organization.Private deployments
Require all new apps to be published as private, restricting access to authenticated team members only
Password-protected deployments
Allow team members to add password protection to their published apps
Private development URLs
Require authentication for all app development URLs, including SSO for SAML-enabled organizations
Ban public apps
Prevent team members from creating public apps that can be forked or viewed by anyone
Private deployments
When enabled, all new apps must be published as private. Private apps are only accessible to authenticated members of your organization. When to use this setting: When to use this setting:- The organization handles sensitive data or proprietary applications
- You need to ensure apps are not accidentally made public
- Compliance requirements mandate restricted access to published applications
- You need to ensure apps are not accidentally made public
- Compliance requirements mandate restricted access to published applications
This setting applies only to newly published apps. Existing published apps retain their current visibility settings.
Password-protected deployments
Control whether team members can create password-protected deployments. When enabled, builders can add an additional layer of security by requiring a password to access their published apps. When to use this setting:- You want to allow sharing apps with external stakeholders without making them fully public
- Teams need to demo applications to clients before wider release
- You require granular access control beyond organization membership
Require private development URLs
When enabled, all app development URLs require authentication. If your organization has enabled SAML, development URLs require SSO authentication. When to use this setting: When to use this setting:- You need to prevent unauthorized access to in-progress applications
- Security policies require all development environments to be protected
- You want to ensure only authenticated team members can view development previews
- Your security policy requires all development environments to be protected
- You want to ensure only authenticated team members can view development previews
Ban public apps
When enabled, all new apps are automatically set to private within your organization. Public apps can be forked and have their source code viewed by anyone on the internet. When to use this setting: When to use this setting:- Organizational intellectual property must remain confidential
- You need to prevent accidental exposure of proprietary code
- Compliance requirements prohibit public code repositories
- You need to prevent accidental exposure of proprietary code
- Compliance requirements prohibit public code repositories
Ban source code export
When enabled, team members cannot export app source code as a zip file. This prevents code from being downloaded and shared outside of the Replit platform. When to use this setting: When to use this setting:- You need to maintain strict control over where source code resides
- Security policies prohibit local copies of code
- You want to ensure all development happens within managed environments
- Your security policy prohibits local copies of code
- You want to ensure all development happens within your managed environment
Security settings
Security settings help you enforce vulnerability scanning and other protective measures.Require security scan
Configure whether all apps must pass a security scan before publishing. Security scans detect vulnerabilities, exposed secrets, and other security issues in your code. Available options:| Setting | Description |
|---|---|
| Off | Security scans are optional |
| Require | All apps must pass a security scan before publishing |
- Security compliance requirements must be met
- You want to prevent accidental exposure of API keys or secrets
- You need to ensure consistent security standards across all published apps
- You want to prevent accidental exposure of API keys or secrets
- You need to ensure consistent security standards across all published apps
This setting does not apply to apps that were published before the setting was enabled.
Source control settings
Source control settings help you enforce version control practices and protect your organization’s code repositories.Require Git remote
When enabled, all apps must have local changes pushed to a Git remote before publishing. This ensures that all code changes are tracked in your organization’s version control system. When to use this setting: When to use this setting:- All code must be backed up in Git
- You need an audit trail of all code changes
- Workflows require code review before publishing
- You need an audit trail of all code changes
- Your workflow requires code review before publishing
This setting does not apply to apps that were published before the setting was enabled.
Private remotes
Control whether team members can use public Git repositories. When set to require private remotes, team members can only push to private repositories on platforms like GitHub. Available options:| Setting | Description |
|---|---|
| Off | Team members can use public or private repositories |
| Require for non-admins | Non-admin team members must use private repositories |
| Require for all | All team members, including admins, must use private repositories |
- Public code repositories are prohibited
- You need to ensure proprietary code is not accidentally pushed to public repos
- Compliance requirements mandate private version control
- You need to ensure proprietary code is not accidentally pushed to public repos
- Compliance requirements mandate private version control
Best practices
Start with private-by-default
Start with private-by-default
Enable Private deployments and Ban public apps to ensure all new apps are private by default. This prevents accidental exposure of sensitive applications.
Enforce security scanning
Enforce security scanning
Set Require security scan to catch vulnerabilities before apps go live. This helps maintain consistent security standards across your organization.
Protect development environments
Protect development environments
Enable Require private development URLs to ensure even in-progress work is protected. This is especially important for organizations handling sensitive data.
Control source code access
Control source code access
Combine Ban source code export with Private remotes requirements to maintain complete control over code location and access.
Related resources
- Information Security - Learn about Replit’s security practices and compliance standards
- SAML authentication - Configure single sign-on for your organization
- Groups and permissions - Manage team member access with roles and groups